If you aren’t aware, NSX 4.1.1 introduced VLAN filtering capability on the VLAN Transport zones. This feature is important especially when you don’t want your NSX tenants to create segments on VLANs that are meant for infrastructure traffic.
Please check out the release notes here:
https://docs.vmware.com/en/VMware-NSX/4.1.1/rn/vmware-nsx-411-release-notes/index.html
VLAN filtering can also be done on the overlay transport zones to control the VLANs used for guest VLAN tagging (VGT) on the overlay segments, but I think this functionality already existed. In this article, we will discuss both scenarios:
- VLAN filtering on NSX VLAN transport zone
- VLAN filtering on NSX overlay transport zone
Let’s get started:
Current environment
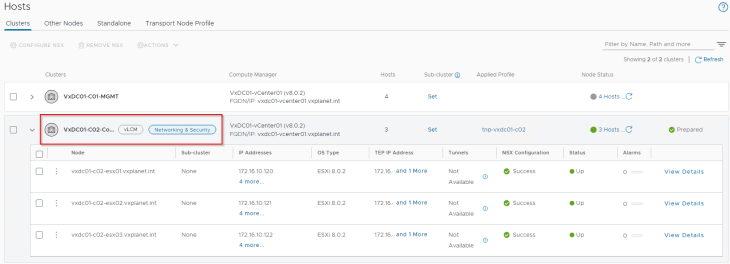
Before we jump in, let’s review the current home lab environment I prepared for this article.The current lab environment has two vSphere clusters:
- Management cluster (VxDC01-C01-MGMT) which hosts all the management plane components. This cluster is VLAN backed and is not prepared for NSX.
- Compute cluster (VxDC01-C02-Compute) which hosts the workloads. This cluster is prepared for NSX.

Both clusters are on separate vCenter VDS. The compute cluster is prepared with a transport node profile, currently only on the default overlay transport zone. We will add VLAN transport zones later.

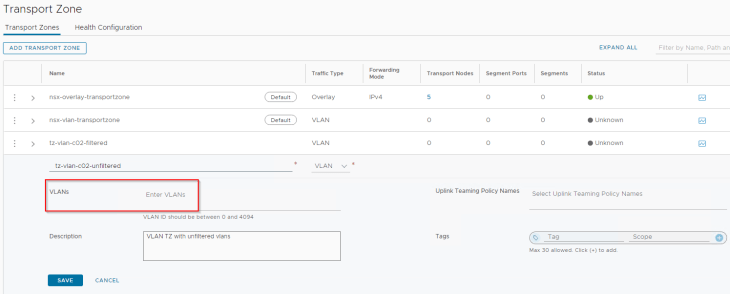
We have pre-created two VLAN transport zones:
- tz-vlan-c02-filtered : allows VLANs 1001 and 1005
- tz-vlan-c02-unfiltered : allows all VLANs (unrestricted)

We have the below VLANs currently in use (in vCenter) for the infrastructure traffic:
- VLAN 1001 – Management
- VLAN 1002 – vSAN traffic
- VLAN 1003 – vMotion traffic
- VLAN 1004 – Host TEP traffic
- VLAN 1005 – VM traffic (General workloads)
- VLAN 1006 – Edge BGP peering (ToR A)
- VLAN 1007 – Edge BGP peering (ToR B)
- VLAN 1008 – Edge TEP traffic
- VLAN 1009 – NSX ALB VIP network
Our objective is to prevent NSX tenants from using the infrastructure VLANs to provision NSX segments.
VLAN filtering in NSX VLAN transport zone
Let’s see what happens when we associate the VLAN transport zone “tz-vlan-c02-unfiltered” to the compute cluster. For this we link the transport zone to the transport node profile.
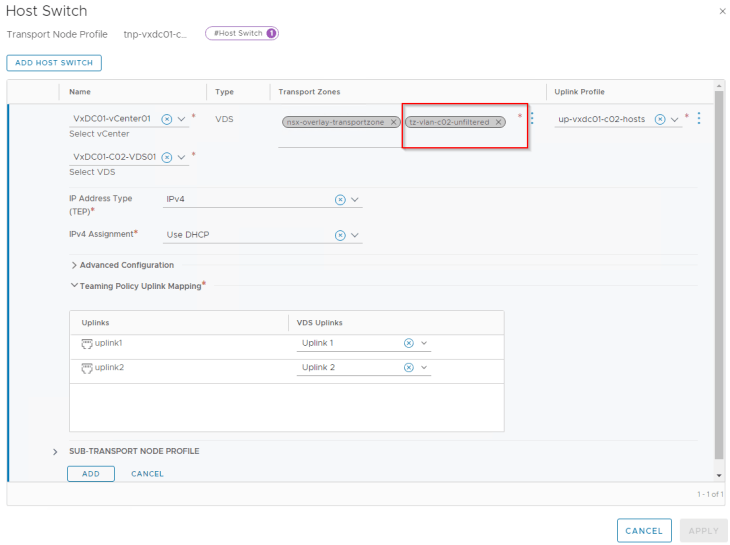

As this transport zone has unrestricted VLANs, NSX tenants would be able to create segments on the VLAN of their choice, say for example VLAN 1002 which is the VLAN for vSAN traffic.


Which is something we need to restrict.
Let’s replace the transport zone “tz-vlan-c02-unfiltered” with “tz-vlan-c02-filtered” that only allows VLAN 1001 and 1005 to be used by the tenants.



Notice that, the NSX tenants can now only create VLAN segments from the allowed list. For eg: an attempt to create a segment on VLAN 1002 (vSAN) will be rejected, but a segment on VLAN 1005 will succeed.


Similarly, we could also define VLAN filtering on the VLAN transport zone used for NSX edge TEP and uplinks. In this case we will only allow VLANs 1006 (BGP peering to ToR A), 1007 (BGP peering to ToR B) and 1008 (Edge TEP), as below:

VLAN filtering in NSX Overlay transport zone
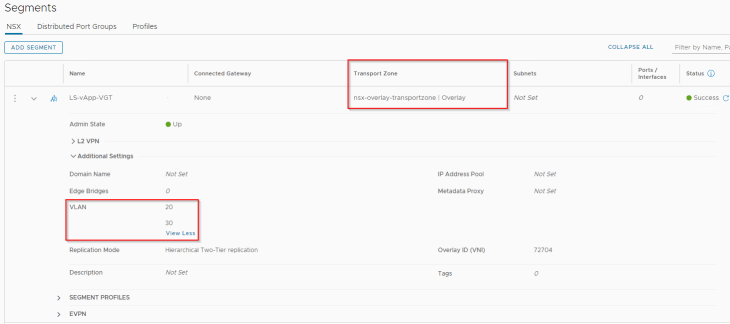
VLAN filtering can also be done on the overlay transport zones to control the VLANs used for guest VLAN tagging (VGT) on the overlay segments. Let’s associate the VLAN range 20-30 to the overlay transport zone.

Optionally, we can remove the VLAN transport zone associated with the transport node profile for the cluster, but make sure we have the respective overlay transport zone added..

Let’s create an overlay segment and allow VLANs 20 and 30 for guest VLAN tagging. As this is within the allowed range, it should be accepted. Any VLAN outside of the range will be rejected. For eg: we see VLAN 32 is rejected on the segment.

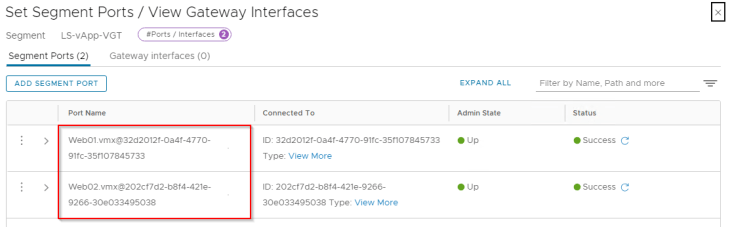
We will now attach two VMs – Web01 and Web02 to this overlay segment.
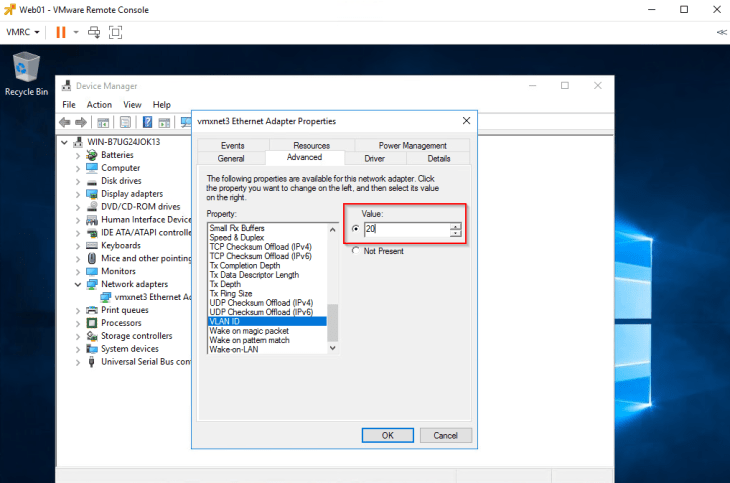
We will enable guest VLAN tagging on the VMs (on VLAN 20) and confirm they are able to communicate to each other.
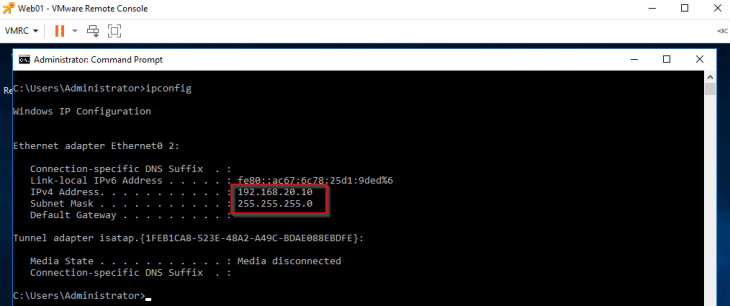
The below snippet is from Web01.

That’s all for this blog post. We will meet again with another NSX topic. Stay tuned!!!
I hope the article was informative, and don’t forget to buy me a coffee if you found this worth reading.