It isn’t a secret that the overwhelming majority of data hosted by enterprises in the cloud is with US-owned cloud providers. But a study by the Centre for European Policy Studies in 2021 found that a whopping 92% of the western worlds data is currently stored in the US. In principal that has been fine with organisations based in other countries, since the scale of these cloud providers was such that data locality was not a problem. The relevant security controls and technologies also exist to protect the data from unauthorised third parties.
Politically however, the landscape is changing. The majority of the worlds population has privacy regulations inline with GDPR. The number of countries implementing data privacy laws has been increasing annually, for both personal and enterprise data. Furthermore, the very definition of personal information is evolving with our online presence, and it’s only going to get more complex over time.
Thanks to the US Clarifying Lawful Overseas Use of Data (CLOUD) Act of 2018, courts can instruct US companies to collect data on systems they manage, not just on US soil, but in theory anywhere in the world. Separately, in July 2020, the Court of Justice of the European Union (CJEU) made judgement on a case that essentially invalidated the EU/US Privacy Shield framework for transferring data outside of the EU.
-
BEST Webhosting
Explore a comprehensive array of web hosting services designed to cater to various needs. Whether you’re an individual looking for reliable personal hosting or a business requiring high-performance solutions, BEST Webhosting offers tailored options to ensure optimal website performance, robust security, and 24/7 support.
-
Unveiling the Pillars of Web Hosting
Web hosting is the backbone of a digital presence, providing the infrastructure necessary to publish and maintain websites online. This article delves deep into the essentials of web hosting, guiding individuals and businesses to make informed decisions. Learn about hosting types, server performance, and scalability options to choose the perfect fit for your online goals.
-
Digital Experience and Coding a New Website
Building a website today involves more than creating an online presence; it’s about delivering an exceptional digital experience. This piece explores modern website design principles, user experience strategies, and advanced coding techniques. It highlights how a well-crafted website can effectively convey your brand message, captivate audiences, and drive business success.
-
How to Buy a .com.au Domain: A Buyer’s Guide to .com.au Domains
This guide is a must-read for startups and established businesses aiming to enhance their Australian online presence. Learn the steps to secure a .com.au domain that aligns perfectly with your brand identity. The article provides insights into domain registration requirements, tips for choosing a memorable domain name, and the benefits of a local domain for SEO.
- Incredible Ideas deserve Incredible DomainsWith Rapid Registration, your domain is registered almost instantly, meaning you don’t have to wait to get your business or name online!
-
Edge of Technology, Digital Transformation, and Cloud Computing
Staying competitive in today’s fast-paced digital landscape requires leveraging cutting-edge technologies. This article explores the vital roles of Digital Transformation (DT) and Cloud Computing in modern business strategies. Understand how these technologies drive efficiency, foster innovation, and enable organisations to scale operations seamlessly.
-
The Best WordPress Plugins for Email Marketing to Grow and Engage Your Subscriber List
Email marketing remains a powerful tool for audience engagement and lead conversion. Discover top WordPress plugins like Mailchimp, Constant Contact, OptinMonster, and Thrive Leads. This article provides detailed guidance on creating effective opt-in forms, segmenting email lists, automating campaigns, and tracking metrics for successful email marketing strategies.
-
The Best WordPress Caching Plugins to Optimize Site Speed and Performance
Website speed and performance are crucial for user experience and SEO rankings. This detailed review covers the most effective WordPress caching plugins, including W3 Total Cache, WP Super Cache, WP Rocket, WP Fastest Cache, and LiteSpeed Cache. Learn how these plugins enhance site performance by minimising load times and optimising server resources.
This isn’t just a European concern either, it’s on the radar across other regions on a global scale. Legal cases and fines are starting to arise for organisations incorrectly interpreting GDPR, and there are still open questions about how legislation will be enforced internationally.
These are not isolated instances, and in conjunction with an increased risk of data breaches and more sophisticated cyber attacks, companies are starting to seriously consider repatriation of data stored overseas. Through the global network of VMware Cloud Provider Partners (VCPP), and the VMware Sovereign Cloud framework, VMware have the means to implement data sovereign solutions locally across any region.


VMware Sovereign Cloud is a framework of guiding principles and best practices to help partners deliver cloud services that adhere to the data sovereignty requirements of a specific jurisdiction. A sovereign cloud framework does not replace public cloud, nor does it replace industry compliance. In fact the opposite is true, the sovereign cloud framework seeks to augment existing platforms and regulations, with a specific focus on putting the customer in complete control of their data.
This control is derived by providing both data residency and data sovereignty with full jurisdictional control. Data residency relates to where the data is physically and geographically stored and processed. Due to the extreme scale of the main public cloud providers, this is something they are usually able to provide. Often though, metadata (data about the data) can leak out into other regions, typically the US. In some cases, data residency alone is not sufficient to ensure compliance with data privacy laws. Data sovereignty relates to law, specifically data being subject to the governance structure, and more importantly jurisdiction, of the nation where the data is processed and stored.
Data still needs to be accessible, and this is a really important point. A sovereign cloud solution needs to not only protect critical data, but also unlock its value. Data can be extracted in a meaningful way, for both private and public sector organisations, whilst providing transparency around architecture and operations.
As an example, both my banking and health records are stored extremely securely in a data centre, with a bunch of regulatory and audit processes in place. However, I can access these records on-demand using my mobile phone, which is a device my bank and my healthcare provider has no control over. Equally, there may be times when others need to access the same records, either anonymised or with personal identifiable information. Like if I applied for a credit-based financial service, or if I was referred to a healthcare specialist for a specific condition. Data sovereignty isn’t about locking up data and making it inaccessible.
Clearly, data still needs to be accessible to the right people through an end client, device, or system, whilst maintaining the integrity of the data. It is important therefore, to have an example architecture for how data can be exchanged, or act as a landing platform for data collected from member states and repatriated from other regions. In implementing such an architecture, a national capability for the digital economy can be achieved, whilst securing data with audited security controls, and ensuring compliance with data privacy laws.
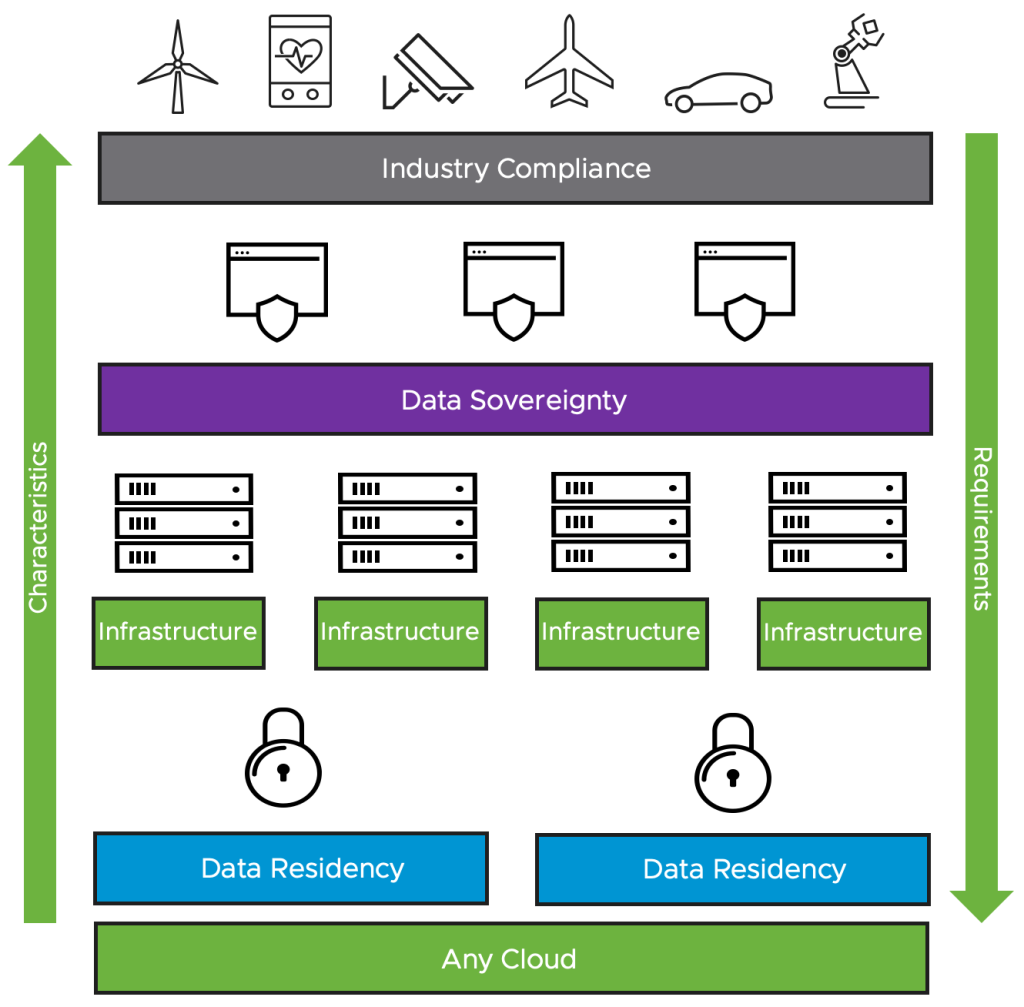
The basis of a VMware Sovereign Cloud is the VMware reference architecture, in the form of VMware Validated Solutions (VVS) and the VMware Cloud Provider Partner (VCPP) stack. There is no need for a dedicated sovereign cloud reference architecture. Instead, an overlay is being introduced to organise the infrastructure into different security classifications and domains. This separation of security domains ensures there is no data leakage, of either primary data or metadata, outside of the required locality and jurisdiction.
The VMware Sovereign Cloud framework uses transparent, standardised, software-defined architectures along with a number of key principles and best practises:
- Data sovereignty and jurisdictional control
- Control, authority, and operations are fully managed within the jurisdiction of the nation state where that data was collected
- Data access and integrity
- Cloud infrastructure is resilient across at least 2 data centre locations within the jurisdiction, with secure and private connectivity options
- Data security and compliance
- Information security management system controls are audited and applied inline with industry recognised standards
- Data independence and mobility
- Data and application portability with modern application architectures to prevent lock-in
These key principles deliver benefits such as increased security, improved control, and continuous compliance, whilst future proofing services and unlocking the power of data. National and sovereign digital capabilities can be developed, with national data pooled together to fuel economic innovation and growth.
The VMware Sovereign Cloud provider sets up an audited and approved cloud architecture for the customer in the relevant locality and jurisdiction. Each sovereign cloud must have at least 2 security domains within it. A typical example of a security domain will be built in software, with every IT system or data classification representing one or more security domains.
Security domains provide a common authentication and authorisation boundary. The perimeter is typically protected by things like firewalls, access control, and application filters, whilst services like micro-segmentation can provide further optional security inside the security domain itself. You can think of a security domain as a logical network connectivity area with a common security posture, they can be built specifically to house top-secret data, secret data, restricted data, and so on . The 2 types of security domains are as follows:
- Sovereign domain
- Used to connect out to other services, similar concept to a DMZ, this security domain features the highest level of security and risk mitigation
- Resident domain
- Stores and processes data, will only accept connections from its parent sovereign domain or other trusted resident domains in the same jurisdiction, this security domain features the highest level of trust and confidence
Security domains can be used to make secure connections out to other environments, such as the customers private cloud, or a commercial public cloud provider. The sovereign cloud architecture ensures that if the service is paired with commercial clouds, then no data or metadata is leaked or escapes the sovereign cloud boundary.
The screenshot below is taken from the VMware Sovereign Cloud Technical Whitepaper, which provides a technical deep dive into the aspects and examples of sovereign cloud architectures and integrations. It shows how a sovereign cloud provider can host an application, whilst still consuming the benefits of public cloud services from AWS, Azure, Google, etc.
In this example, the data is encrypted and replicated between the sovereign cloud compliant provider and the public cloud, with the encryption keys only stored on the KMS server with the compliant provider. Other methods can also be used to integrate with third party tooling, such as anonymising data, or replacing sensitive data with specific key pair values that can then be mapped back on the sovereign cloud compliant provider.

You can find a local VMware Sovereign Cloud provider, from the likes of Telefonica, UK Cloud, and OVH, on the VMware Cloud Provider Services page. Further reading material that may be of interest around sovereign cloud and the Gaia-X project in Europe is listed below.
Gaia-X is a broader project beyond sovereign cloud, that attempts to build a federated cloud ecosystem of data, infrastructure, and service providers. The aim is to deliver European digital sovereignty with a future cloud architecture, whilst controlling the flow of data for an overarching state through different legislation boundaries.
Data assets should be able to move freely between approved providers, with both parties providing tools to assist with the migration process to prevent lock-in. Access permissions and data usage controls will travel with the data as it moves through the ecosystem. As with sovereign cloud, the hyperscalers are not excluded and can still participate, providing data sovereignty remains intact. VMware are contributing to the development of the Gaia-X reference architecture as a day 1 member.